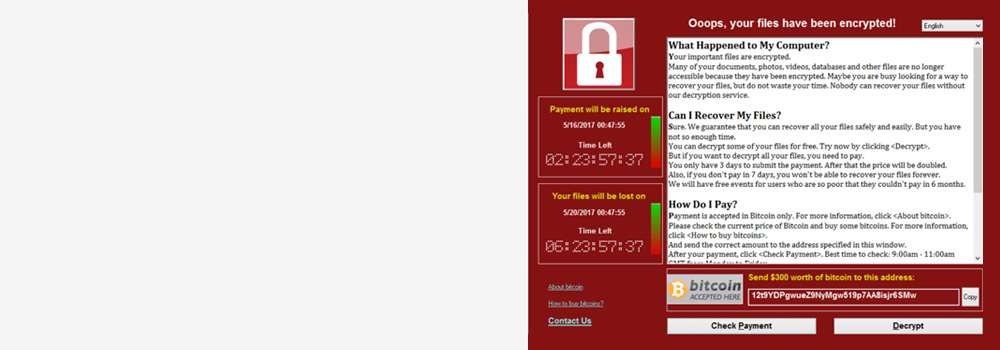
When ransomware encrypts files, professional data recovery companies use advanced tools, techniques, and methodologies to recover the data without paying the ransom. Below are the methods employed by our recovery experts to decrypt ransomware data:
1. Ransomware Identification
- How it works: The first step is identifying the ransomware strain (e.g., WannaCry, LockBit, REvil) to determine if a public decryption tool exists or if known vulnerabilities can be exploited.
2. Public Decryption Tools
- How it works: Utilising decryption tools provided by cybersecurity organizations for specific ransomware strains.
3. Shadow Copy Restoration
- How it works: Attempting to recover data from Volume Shadow Copies created by Windows before encryption occurred.
4. Backup Restoration
- How it works: Recovering data from offsite or disconnected backups if available.
5. Brute Force Decryption
- How it works: Using advanced algorithms to break weak encryption keys.
6. Analysing Ransomware Flaws
- How it works: Exploiting coding or cryptographic errors in the ransomware to retrieve encryption keys.
7. Reverse Engineering
- How it works: Deconstructing the ransomware’s code to understand its encryption mechanism and identify weaknesses. Requires advanced forensic expertise.
8. Negotiation with Attackers
- How it works: In certain cases, we can negotiate with attackers to obtain the decryption key.
9. Forensic Data Recovery
- How it works: Extracting unencrypted data fragments from damaged or partially encrypted files.
10. Data Recovery from Alternate Locations
- How it works: Scanning for unencrypted data in temporary storage, cache, or hidden system areas.
11. File Header Analysis
- How it works: Reconstructing partially encrypted files by analysing and repairing file headers.
12. System Restore Points
- How it works: Reverting the system to a previous state using restore points created before the ransomware attack.
13. Network Packet Analysis
- How it works: Capturing and analysing network packets during the encryption process to identify the encryption key.
14. Decryptor Development
- How it works: Developing a custom decryptor tool based on forensic analysis of the ransomware.
15. File System Metadata Recovery
- How it works: Recovering data from file system metadata or unencrypted portions of the disk.
16. Key Escrow Servers
- How it works: Analysing ransomware’s communication with command-and-control servers to intercept encryption keys.
17. Registry Analysis
- How it works: Examining the Windows registry for stored decryption keys or ransomware artifacts.
18. Using Cryptographic Libraries
- How it works: Leveraging known cryptographic libraries used by ransomware to simulate key generation.
19. Memory Dump Analysis
- How it works: Dumping the system’s memory to search for encryption keys or ransomware artifacts.
20. Artificial Intelligence (AI) Techniques
- How it works: Using AI and machine learning algorithms to predict decryption keys or repair encrypted files.
Why Professional Ransomware Recovery Is Essential
- Expertise in identifying ransomware strains and deploying the correct recovery methods.
- Access to advanced tools and forensic labs.
- Mitigation of further data loss or reinfection.
Birmingham Data Recovery Professional Forensic data recovery companies continuously adapt to evolving ransomware techniques, ensuring the best possible outcome for data recovery.